Network segmentation is a fundamental practice in modern network design aimed at enhancing performance, security, and manageability. By dividing a larger network into smaller, isolated segments, organizations can control the flow of traffic more effectively, minimize the impact of potential security breaches, and streamline network management. This process involves using various technologies, such as Virtual Local Area Networks (VLANs), network bridges, and routers, to create distinct network segments that serve different purposes or functions.
Segmentation helps in optimizing network performance by reducing congestion and improving resource allocation. It also bolsters security by containing potential threats within specific segments, thereby preventing them from spreading across the entire network. Additionally, network segmentation simplifies troubleshooting and maintenance, allowing for more focused management of individual segments.
In essence, network segmentation is a strategic approach to designing a robust and efficient network infrastructure, ensuring that each segment operates optimally while maintaining overall network integrity.
Segmentation vs. Subnetting
Network segmentation and network subnetting are related but distinct concepts in network design.
Network Segmentation involves dividing a larger network into smaller, more manageable segments or sub-networks. This process aims to improve performance, enhance security, and simplify network management. Segmentation can be achieved using various techniques, including VLANs (Virtual LANs) and physical network boundaries. The primary goal is to reduce broadcast domains, limit the scope of network issues, and isolate different types of traffic or users. For example, a company might segment its network to separate departments like finance and HR to limit broadcast traffic and enhance security.
Network Subnetting, on the other hand, refers specifically to the practice of dividing a larger IP network into smaller subnetworks, or subnets. This is done by creating subnet masks that define the range of IP addresses available within each subnet. Subnetting allows for more efficient use of IP addresses, better organization, and isolation of traffic within an IP network. It is a method used to manage and optimize IP address allocation, often within a single organization’s network. For instance, a large organization might use subnetting to allocate different IP ranges to various departments or geographical locations.
In summary, while both network segmentation and subnetting involve dividing a network into smaller parts, segmentation is a broader concept that includes various methods for managing and isolating network traffic, while subnetting specifically deals with dividing an IP address space into smaller, manageable subnets.
Network Bridges
A bridged network connects two or more network segments, allowing them to act as a single network. This is achieved through a device called a network bridge, which operates at the data link layer (Layer 2) of the OSI model.
A network bridge is a device or software that connects two separate network segments, making them function as a unified network. This is particularly useful in scenarios where you need to extend the reach of a network or integrate different network segments without requiring them to be on the same physical network infrastructure. Docker containers can communicate with each other using software bridges, for example.
How It Operates
a. Packet Forwarding
When a network bridge receives a data packet, it examines the packet’s MAC (Media Access Control) address. It then determines whether to forward the packet to the other segment based on the destination address. Here’s how it works:
- Learning: The bridge builds a MAC address table by learning which MAC addresses are present on each segment. It records which addresses are associated with which segment.
- Forwarding: When the bridge receives a packet, it checks the destination MAC address against its MAC address table. If the address is on the same segment, the bridge does not forward the packet to the other segment. If it’s on a different segment, the bridge forwards the packet to that segment.
- Filtering: The bridge can also filter packets based on MAC addresses to reduce unnecessary traffic and enhance network performance.
b. Spanning Tree Protocol (STP)
To avoid loops and ensure that there’s only one logical path between all network segments, bridges use the Spanning Tree Protocol (STP). STP helps in maintaining a loop-free topology by:
- Detecting Loops: Identifying potential loops in the network.
- Blocking Redundant Paths: Temporarily disabling redundant paths that could create a loop.
- Reconfiguring Paths: Enabling blocked paths if the primary path fails, ensuring network reliability.
3. Types of Bridges
- Transparent Bridges: These are the most common type, operating transparently to the devices on the network. They forward packets based on MAC addresses and do not alter the packets themselves.
- Source Route Bridges: These require devices to include routing information in their packets. This type is less common and is typically used in specific legacy environments.
- Multi-port Bridges: These bridges have more than two network interfaces, allowing them to connect more than two segments. They function similarly to transparent bridges but can handle more complex network topologies.
4. Use Cases
- Extending a Network: Bridging can be used to extend the range of a network, such as connecting a wireless network segment to a wired segment.
- Integrating Different Network Segments: It helps integrate separate network segments, such as connecting different office floors or departments while keeping them on the same logical network.
- Segmentation and Traffic Management: Bridging can segment network traffic, which can help in managing and controlling broadcast traffic within different segments.
5. Advantages and Disadvantages
Advantages:
- Simplicity: Bridges are relatively easy to set up and manage compared to more complex routing solutions.
- Network Segmentation: They allow for the segmentation of networks without creating separate networks.
- Reduced Collision Domains: By separating segments, bridges help reduce the collision domain, thereby improving network performance.
Disadvantages:
- Limited Scalability: As networks grow, the complexity of managing bridges increases, and they may not scale as efficiently as routers.
- Potential for Loops: Without proper loop prevention mechanisms like STP, bridges can create network loops that can lead to broadcast storms.
Comparing a bridge with a router and switch
A bridge operates at the Data Link Layer (Layer 2) and is used to connect and filter traffic between network segments. It examines MAC addresses to determine whether to forward or block packets, effectively segmenting the network to reduce collision domains and manage traffic. Bridges are ideal for extending networks and managing broadcast traffic within the same network.
A router, on the other hand, functions at the Network Layer (Layer 3) and is used to connect different networks, such as connecting a local network to the internet. Routers make forwarding decisions based on IP addresses and are responsible for routing traffic between distinct networks or subnets. They handle tasks like packet forwarding, network address translation (NAT), and routing protocols to ensure data is delivered across diverse networks.
A switch also operates at the Data Link Layer (Layer 2) but differs from a bridge in that it connects multiple devices within a single network segment. Switches use MAC addresses to forward frames only to the specific device they are intended for, creating multiple collision domains and improving network efficiency compared to hubs. Advanced switches can also operate at Layer 3 for routing functions, combining some features of both bridges and routers.
In summary, while bridges connect and manage traffic between network segments, routers interconnect different networks based on IP addresses, and switches facilitate efficient communication between devices within the same network segment.
VLAN
A broadcast domain is a network of computers (joined by a switch) that can receive broadcast messages. Too many devices on a broadcast domain can have a negative impact on the networks performance. That is one reason why companies split and group their devices in different isolated local area networks (LAN). Another reason is that you can logically group devices together based on their task/purpose. Perhaps some devices should not connect to the internet.
You can have many isolated LANs attached to a single Switch by creating a Virtual LAN (VLAN):
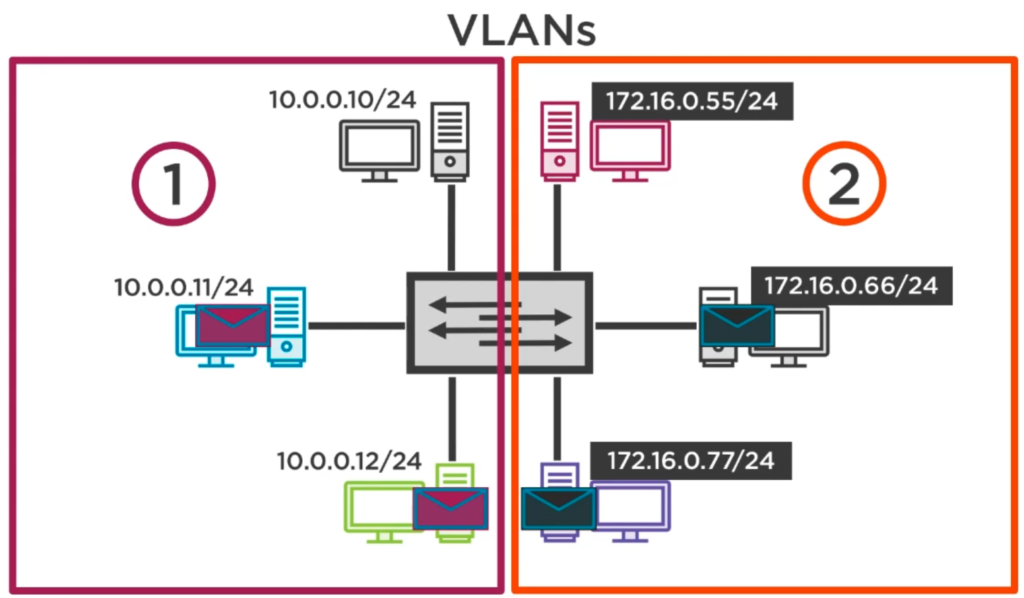
You can even have your devices scattered over several buildings and still have them belong to their own virtual networks! In the following illustration we have such as situation: Two VLANs with devices scattered over two buildings, each building has a Switch, both Switches are connected via a special connection, a so called Trunk Link:
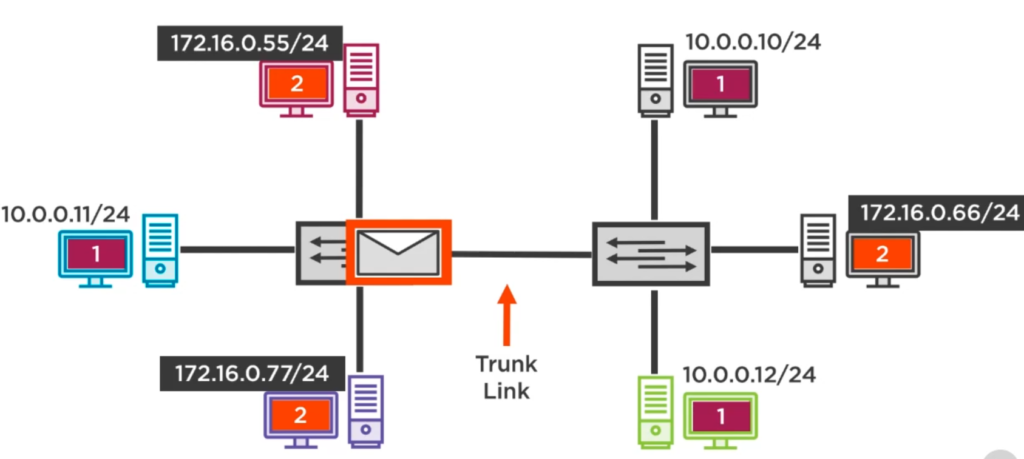
If device 172.16.0.55/24 wants to send a message to device 172.16.0.66/24 in the other building, then it has to pass the Trunk Link. Switch #1 will add information to the frame header to include the VLAN number from where this frame originated: It attaches VLAN #2 tag. The second switch in the other building evaluates the tag, removes it and finally forwards the message. Only traffic that passes the Trunk Link is tagged.
Network Peering
Network peering is a method of interconnecting two networks or systems to facilitate direct communication between them. Network Peering involves establishing a direct connection between two networks so that they can exchange data directly without passing through a third party or intermediary network. This connection is typically used to enhance the efficiency and performance of data exchange.
Types of Network Peering
- BGP Peering: In internet routing, Border Gateway Protocol (BGP) peering is used to exchange routing information between different autonomous systems (ASes). BGP peering allows networks to share routing data and ensure that data packets travel the most efficient path.
- Private Peering: This type involves a direct, private link between two networks, often within the same data center or through a dedicated circuit. It’s commonly used by businesses to connect to cloud providers or data centers.
- Public Peering: In this scenario, networks connect via an Internet Exchange Point (IXP). Public peering allows multiple networks to connect and exchange data through a shared facility, which can improve efficiency and reduce latency.
Benefits of Network Peering
- Reduced Latency: Direct connections usually result in lower latency since data doesn’t need to traverse through multiple intermediate networks.
- Improved Bandwidth: Peering can increase available bandwidth between networks by providing a more direct and dedicated path for data.
- Cost Savings: By reducing reliance on third-party transit providers, organizations can save on data transfer costs.
- Enhanced Performance: Direct peering often leads to better performance and reliability, as it bypasses potential bottlenecks and points of congestion in third-party networks.
Use Cases
- Cloud Providers: Cloud services like AWS, Azure, and Google Cloud offer peering options to connect their cloud networks with customers’ networks. This ensures fast, secure, and efficient data transfers between the customer’s on-premises infrastructure and cloud resources.
- Content Delivery Networks (CDNs): CDNs use peering to enhance the delivery of content by connecting directly with Internet Service Providers (ISPs) and data centers.
- Data Centers: Data centers often use private peering to connect with other data centers or cloud providers to facilitate faster and more reliable data transfers.
Peering vs Bridging
While both network peering and bridging involve connecting networks, peering is focused on connecting distinct networks to improve external data transfer, while bridging is concerned with extending or connecting segments within a single network to ensure internal communication.
